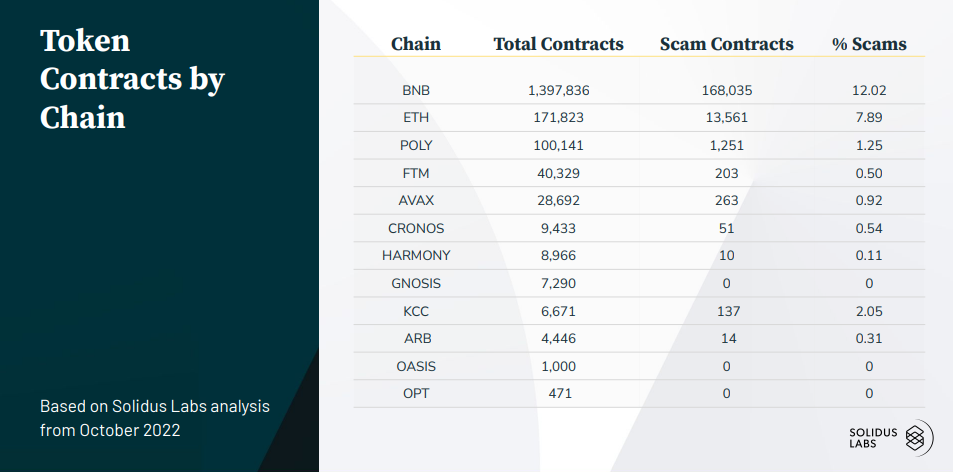
Analysis of Investment Scams by Solidus Labs


We live on a planet where new technology seems to be working against the vast majority of humans living on this planet, rather than helping us to live better. This is sometimes called “singularity”, and Tristan Harris, a former Google ethics guru has now joined a public crusade so that tech companies “stop exploiting our weaknesses” and trying to abuse our confidence, and Yuval-Noah Harari says that we are now being hacked.
However for an engineer or for a scientist, this is not business as usual, these problems actually seem solvable. Potentially decentralization and democracy, freedom of speech and quality journalism, liability lawyers, market regulators and consumer rights advocates, law enforcement, benevolent academics and even tech companies themselves trying to make a difference and playing the long game not trying to cheat all the time, can possibly solve these problems. At least we have been trying. We have not run out of options.
Bitcoin and blockchain technologies have been developed precisely because we deeply mistrust our institutions, banks and governments, and we are now experimenting with alternative ways of doing things. This movement is not over. In particular the role of the private sector is increasing: bitcoin is in many ways private money, and a private system belonging to a group of oligarchs. At the same time the blockchain world has been nurturing a dreamer world of building a new economy with a fresh start: where money is created by the people, and where the wisdom of crowds leads to new types of outcomes, which benefits potentially all the people who dare to participate in it.
Sadly, the tech establishment is not helping, in bitcoin and everywhere else. A vast majority of tech developers have no sense whatsoever of social responsibility. They are sometimes not even trying to make things which actually work, or which are fit for purpose, or they fail to do so in spectacular ways. Deeply entrenched in the tech developer oligarchies, and equally bad at universities, and even worse in the mass and also pretty bad at say armed forces or government agencies, is an anarchic business and personal life disruption ideology. The technology is pushed on people who live on this planet in very crude dystopian forms driven by the desire to create a machine economy driven by the desire to influence and abuse the human element.

Not only that our technology as of today fundamentally lacks network neutrality, as much as it a lacks a positive or ethical purpose: it also does not fulfill the basic role of enabling of business or any other activity, it works primarily for the benefit of the sick, the corrupted, the incompetent. All this gets even more ugly when a lot of money is at stake. You are not happy with governments and bankers, here is what you get.
A new report written on explicit order from US government DARPA agency tells us some inconvenient truths about current Blockchain, Bitcoin and Ethereum world. It is written very much from the perspective of securing a distributed system… which is the main thing these networks are. The discoveries are “shocking”:
In particular we read that:
Trail of Bits based in NY, have an impressive pedigree: They have tens of academic publications on applied crypto, SW exploits, linux kernel etc. They operate “a center of excellence for blockchain security”. Notable projects include audits of Algorand, Bitcoin SV, Chainlink, Compound, Cosmos, Ethereum 2.0, MakerDAO, Matic, Polkadot, Solana, Uniswap, Web3, and Zcash.
Remark: This is serious work and in many ways, a result of years of work. Very different compared to the letter written by Bruce Schneier and 1500 computer scientists which is full of strong opinions and unsubstantiated claims, but fundamentally there is no technical, crypto or cybersecurity content of any sort, no attempt to study or examine these problems. Shame on you Mr. Schneier! An applied cryptography expert who has given up on… applied cryptography some 20 years ago to become a celebrity.
Some interesting facts:
The wholesale price of gas went up 800% in 2021 (FT).
About as much as NVIDIA stock price or bitcoin market price went up in 3 years. The price of industrial sillicon has also surged by some 800% recently (as it did during the 2008-2009 financial crisis). In the same way, the price of Bitcoin and Ethereum have surged by roughly 800% in the last 3 years.
We hope the readers realize that all these events are to some extent related.
Sad day for freedom of speech in cryptography. The self-proclaimed Satoshi Nakamoto Craig Wright has won a legal battle claiming copyright infringement on the part of bitcoin.org for hosting the Bitcoin original whitepaper.
After censorship of Garcia paper (Volkswagen Aktiengesellschaft vs Garcia, et al, EWHC 1832, 25 June 2013). This is another very sad day for cryptography research in the UK.
A very curious statement was issued by Dr Craig lawyers:
“Dr Wright does not(?) wish to restrict access to his(?) White Paper. However, he does not agree that it should be used by supporters and developers of alternative? assets, such as Bitcoin Core, to promote? or otherwise misrepresent? those assets as being Bitcoin given that they do not support??? or align? with the vision for Bitcoin as he set out in his White Paper.”

This shows what it is all about, it is an attempt to challenge the reputation of bitcoin, as the main and the biggest implementation of Satoshi Nakamoto bitcoin. Most likely for profit: bitcoin market cap is 650 Billion US$ at the moment of writing.
Of course that Craig Wright wishes to restrict access to this paper, or at least to attack the vision created by this very paper. It is an attack on the bitcoin ecosystem, community and values. This paper, once published is a public good, and no one should be restricted from accessing it, or sharing it as part of their crypto currency research or development activity. It was initially published anonymously and with a clear intention of being published anonymously. This intention transpires from the paper, and is part of the Satoshi original vision. Bitcoin is expected to be a self-organising anarchic cooperative, controlled mainly by to those who represent the highest hashing power, which people can then decide or influence, basically through the longest chain rule and software updates, which bitcoin system blockchain or software will dominate the crypto payment market. Rather than an old-school private monopoly, controlled by one wealthy individual, unable to gather this type of strong majority support, and using the powers of the courts and the police in order to exclude and intimidate others. .
It is not the first time that Craig Wright is trying to restrict free speech, as in the recent infamous defamation lawsuit for calling Craig Wright a fraud on Twitter and two more defamation lawsuits against McCormack and Ver. Or even more problematic, in his notorious Florida lawsuit. All these litigation events, are clearly malicious and aggressive attempts, to intimidate others, to restrict the freedom of speech in cryptography, and indirectly, the freedom to engage in bitcoin transactions or to fork bitcoin software, as well as the freedom of propagating the original anonymous payment anarchy vision by Satoshi. This regardless whether Satoshi actually existed or not, and regardless what was the role of Craig Wright in early days of bitcoin many years ago.
The main fact about Satoshi, is that an anonymous paper was released in order to create bitcoin, and no one should try to destroy his legacy: of sharing this anonymous white paper and the ideas it contains. One can be critical about some major mistakes it contains (cf. slide 53 here and slide 50 here) of the fact that it talks about CPUs and it did not predict that the network will split into three almost entirely disjoint types of entities: peer nodes, miners, and transacting parties. Anyone can have their own interpretation, and their own blockchain. Everyone should be able to sharing this original file. It is very much like forbidding the church from preaching the gospel. Bitcoin developers are NOT acting as a publisher here, claiming to be or represent a certain Satoshi Nakamoto, or infringing any IP, but rather simply sharing the anonymous or pseudonymous crypto research paper which inspired them. This paper does de facto belong to the public domain. Crypto history knows primarily one single paper written by a mysterious anonymous author.
This is also very clearly how Satoshi intended his paper to be published. I think Satoshi wanted this paper to be viral, and a little bit underground, outside of the mainstream, rather than officially published in some crypto or security conference proceedings. Here the consensus of the academic research community rules, and no court in the world has jurisdiction in academic research ethics. Craig Wright is self-taught crypto entrepreneur, and officially a chief science officer at NChain, but, an interesting question is, is he a scientist or was he ever a scientist? Did he do a PhD in a technical field? Nope. How many papers in cryptography has Craig Wright published? Zero or close,except that he is trying to claim ownership of an old paper, and only after it became very famous. All these defamation cases hinge on one thing, the reportedly great “global reputation” Craig Wright has, which however he cannot demonstrate because it is rather inexistent. His primary academic background is being a lawyer, and his primary public activity is clearly not science, but a never ending stream of lawsuits.
In addition the defendant Cobra, who failed to defend himself properly, which probably he found difficult, expensive and in fact shameful and counter-productive, will have to pay 35,000 GBP to cover CW’s legal costs.
The defendant Cobra has announced on bitcoin.org that he will continue hosting the bitcoin white paper which is published under the MIT licence on bitcoin.org, and that he will not be intimidated by Craig Wright and his UK lawyers. In contrast and sadly, bitcoin core developers on github have surrendered and removed this same paper, claiming that they are just doing a specific implementation of bitcoin. They are simply scared and intimidated to continue sharing this paper, claiming that there is no evidence the Satoshi has released this paper with intention for it to be shared freely. They have just decided to give up on trying to represent the mainstream bitcoin. As a result you should expect bitcoin dominance to decline in the future, and again it will be a somewhat self-inflicted misery.
Shame on you bitcoin developers who are visibly scared to live the Satoshi legacy in full out of fear of legal retaliation! I encourage all people to propagate, share, and copy the Satoshi visionary paper, as it was shared and propagated for more than a decade.
Open source development can be malicious, and for example it is extremely easy to infiltrate linux source code with dubious code, and banning university researchers from contributing to Linux does not help. It is like killing the messenger for bringing bad news.
This brings us to another question of censorship, cryptographic backdoors and wrongdoing at the very heart of bitcoin community.
It is June 2021, and why does the web site bitcoin.it, which is an extremely popular near-official bitcoin wiki website, still fraudulently claims today that “Bitcoin has a sound basis in well understood cryptography” see here, while omitting to simply mention the name of the peculiar bitcoin elliptic curve, namely the secp256k1 ??? Why the name is taboo??
They emphasise ECDSA, which is an already controversial crypto standard with deeply unclear and confused provable security status in crypto community, and they refer to payment standards endorsed by
by the US Government and used in credit card payments. However bitcoin precisely does NOT obey any of these traditional payment standards such as the elliptic curve endorsed and recommended by US government NIST and the NSA which was until recently a different curve secp256r1, also known as P-256, today replaced by its successor P-384.
Who will believe that the authors have just accidentally omitted to mention the name of the actual bitcoin elliptic curve secp256k1 here… Or was it in order to avoid a critical reader from finding information about this extremely controversial cryptographic primitive used in bitcoin and other cryptocurrencies which however no one else in mainstream crypto engineering world world really vouch for or approve of?
Here is an old blog post on this topic and here are some slides from 2015. It seems that the bitcoin wiki is trying to hide some significant facts about bitcoin… from the users of the financial system called bitcoin. This is is simply irresponsible and this sort of dubious propaganda where bugs are presented as features has been going on for nearly a decade now.
Edward de Bono, scientist and writer, inventor of the concept of “lateral thinking”, died on 9 June 2021, aged 88.
In 1994 he proposed the famous concept of IBM dollar, which is a bit like the father of bitcoin, in several ways:
This last component is maybe missing today: IBM was a rock solid industry player for a very long time. In contrast very few crypto companies have some sort of solid reputation and intrinsic market value outside of making crypto currency itself. Many crypto coins of today are bound to collapse tomorrow. Ethereum and Bitcoin are incredible and they are champions of the “network effect”, but their dominance is not certain, as their deficiencies are widely known. If so, tomorrow other crypto coins can easily dominate. Like Internet Computer, emerged in no time out of limbo, and already is one of the major players.
So far proper industry firms such as say Apple or Samsung, or proper customer-facing large businesses such as Starbucks, have not issued crypto currency. Swiss banks did not either. Only Facebook announced it will issue crypto currency, however Facebook does not make things which people want to buy, they are an opportunistic data-hungry troll factory aiming at controlling the whole world, and their reputation is not great. So as a matter of fact, we are still looking forward to see the IBMs of our times to actually issue some digital currency and fulfil the dream of DeBono. This has not yet happened.
Remark: If GPU makers NVIDIA and AMD profit from the crypto currency prices going to the moon, they do not officially endorse crypto currencies or not yet.

Charlie Hebdo has released a cartoon which has infuriated half of the British empire plus 5000 more fascists in Poland and 200 more crypto fascists.
After a decade of heavily government-sponsored propaganda about quantum computers, we are finally discovering the truth. RSA is NOT secure, not even against normal computers.
Edited and added in 2021-2023:
The story in unfolding slowly and so far can be summarized as follows:


Best period in crypto history ever.
ADDED 6 Feb 2021: traders who trade altcoins will be interested in this.
Yes, the market cap of all crypto currencies combined has reached 1 Trillion US dollars, see also top line ticker here. I have predicted this 3 years ago, after the market collapsed, and now it is a fact: we are past 1T$, however much market cap valuations of this kind are highly questionable.
Unrealistic inflation of figures reported is common in competitive technology sector: look at all advertisements about speed of computer hard drives… totally unrealistic figures and fake news. However we accept the bitcoin market cap benchmark, simply because everybody uses and understands it. It is a de facto standard.
If we compare it to gold and some bankers actually agree with that, the total market cap of all gold on our planet is about 3 trillion (estimates vary). Gold is also subject to HODLing by US and Russian government etc. A tiny quantity of gold is actually ever exchanging hands: similar to bitcoin. An artificial valuable commodity manipulated by powerful actors.
Conspiracy theories suggest that All Time High (ATH) should happen on 9 January, anniversary of the bitcoin Genesis block, and here we are: bitcoin crosses 40 K exactly 3 years after reaching 20K. This confirms the idea that these markets are manipulated (by banks, governments and rich investors). Market manipulation is basically allowed!
Now both bitcoin and gold are actually valuable BECAUSE these powerful actors care about them and because of their tremendous brand value and popularity. Hundreds of millions have been spent on software development and on mining hardware etc. This alone explains the intrinsic value of bitcoin.

So far as of 2021 bitcoin lags behind gold. 12 years after creation bitcoin is still young. In fact, way fewer investors and bankers believe in bitcoin than in Gold, and it is going to stay that way in 2021. Bitcoin is a hard sell in the world of investment managers but eventually people see that no, Gold is not a great investment either but both can be used for portfolio diversification. We probably need another big cycle, wait until 2025 or 2030 for digital currency to become more important than gold. And the winner will probably not be bitcoin, but something technically vastly superior. The Google of cryptocurrency, doing the job right and achieving worldwide dominance… which has probably not yet been invented…
This will however inevitably happen in my opinion. One day crypto currency will reach 3 trillion and gold will continue being eroded. I can hardly imagine otherwise just for practical reason: digital currencies and gold are simply siting at two opposite sides of the spectrum on practicality and relevance in the modern economy.
In the long run, the winner is the digital currency. It will inevitably take over the world and pass the 3 trillion mark and I expect that this will happen in the next decade: before say 9 January of 2030.
In this attack a differential propagates with difficulty for some 20, 40 and up to 64 rounds. We can say that the propagation encounters some “friction”, because the non-linear functions do not always behave as the attacker would like them to behave. Everything looks normal and this is what happens for all block ciphers all the time.
But then for 65, 80, 128 and more rounds, the propagation becomes easier and easier, the friction disappears, the differentials are reproduced MORE easily. This is for EXACTLY the same cipher spec, with different keys though. At the end of the day we discover that this block cipher configuration is not secure no matter how large is the number of rounds, and for any key.

Interestingly when we study what happens locally, say for up to 32 rounds, nothing unusual is observed and the ciphers exhibits no unusual behavior when the number of rounds is small.
This result was presented at ICISC 2020 in Seoul, Korea on 3 December 2020. We call this type of behavior “Non-Markovian propagation” and it is quite rare.
In addition we are able to transform a bug, or an outlier, something which researchers normally discard as inconvenient and problematic, into a feature. We show that this property helps the attacker, and it helps absolutely a lot, to the point that the cipher is never actually secure.
Some most interesting results in cryptanalysis are when something quite unexpected happens… contrary to the intuition ans contrary to the philosophy of 99.999% of ciphers ever made or studied: where authors systematically and maybe naively assume that probabilities do multiply and that they will decrease exponentially when you iterate the cipher. If so, it is sufficient to test a reduced-round version for high probability differentials. Here the probabilities decrease initially at an exponential rate, but later they behave abnormally and stay bounded by a small constant forever.

A cipher can be insecure, even though it has no large probability differentials locally: it is a global long-term property only visible for a larger number of rounds like 64 or more, and only for very few special differences.
Here are the slides presented in normal / extended version.
And here is a recorded video of my presentation.