Now we’ve covered why privacy is essential for widespread cryptocurrency adoption, and how stealth addresses can help assist the pseudonymity (stealth addresses defined and explained in Part 2, pseudonymity discussed in Part 1), it’s time to explain how to combine cryptography and Ethereum’s smart contract functionality to add another layer of obfuscation to public blockchains!
COOL THING 2: RING SIGNATURES
Ring signatures generally satisfy several essential properties, namely anonymity, unforgeability, and collusion resistance. The definition of anonymity here is that an adversary has no more than a negligible advantage of correctly identifying the individual that produced the signature.
Ring signatures offer honestly participating users with ‘unconditional anonymity’, and are formed without a complex setup procedure or the requirement for a trusted third party, trusted setup, or any form of group leader. Users are simply required to be part of an existing public key infrastructure.
Ring signatures are constructed in a way that the ring can only be ‘completed’, and so will only verify correctly, if the signer has knowledge of some secret information, most commonly a private key corresponding to one of the public keys in the ‘ring’. This is done through a zero-knowledge proof of membership.
In the signature generation algorithm, a number is generated at random for each of the other public keys in the ring, and then the signer uses the knowledge of their own private key, or some other ‘trapdoor information’, to ‘close’ the ring.
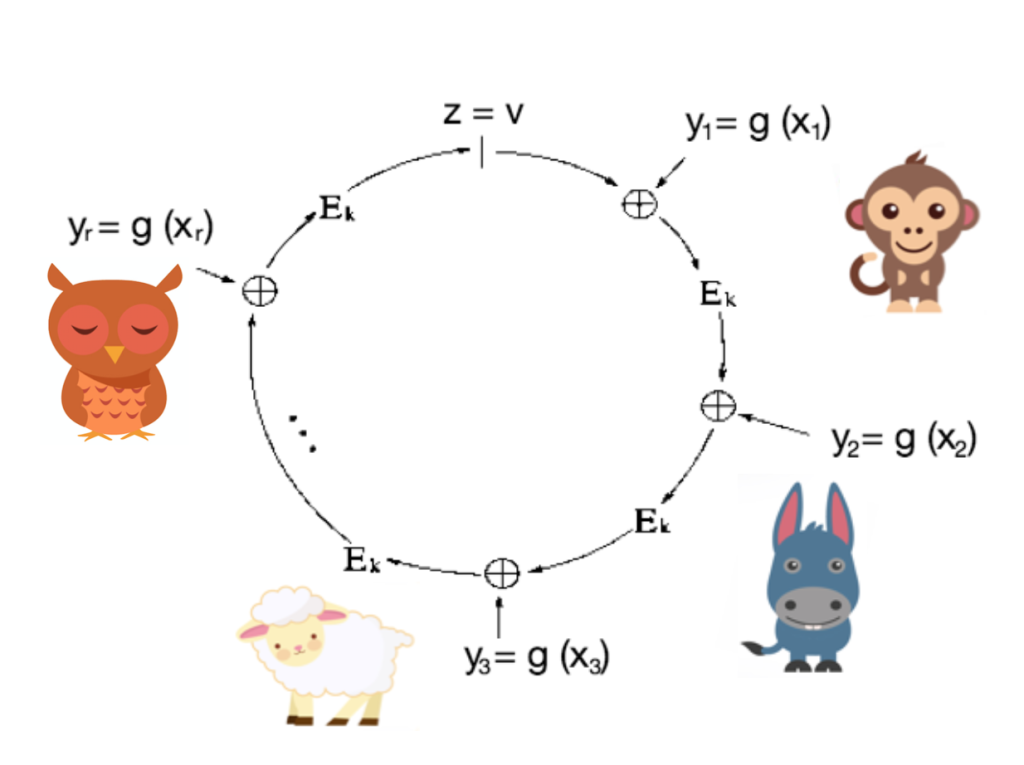
Ring signatures offer users anonymity by hiding transactions within a set of others’ transactions. If there are many users contributing very similar amounts to a ring, then the ring is said to have good liquidity, meaning the transactions can occur quickly, and also that transactions can be effectively mixed, with a high resistance to attempted mixing analysis attacks.
Linkable ring signature algorithms provide a scheme that allows users to sign on behalf of a group, again without revealing the individual signer’s identity, but with the additional property that any signatures produced by the same signer, whether signing the same message or different messages, have an identifier, called a tag, linking the signatures. With this tag, third parties can efficiently verify that the signatures were produced by the same signer, without learning who that signer is.
In our case, we use linkable ring signatures in a mixing contract.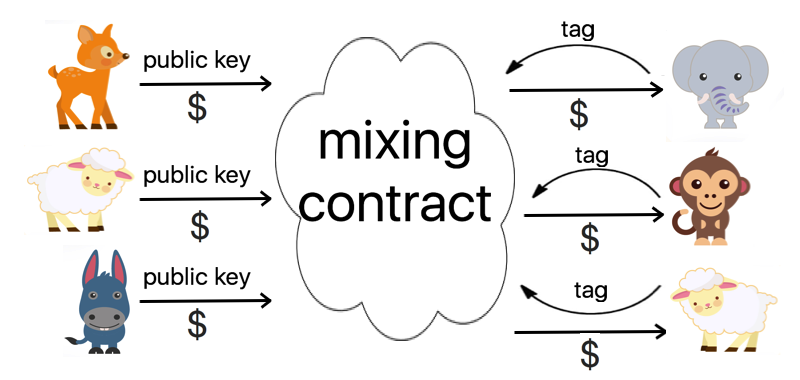
Ring Signature Mixing Contract
Our linkable ring signature scheme relies on the hardness of EC-DDH, and the general scheme is as follows:
- A contract is made to verify ring signatures, receive and distribute coins. Parameters for the specific mix (such as the transaction value of each amount to be deposited into the ring, or the minimum number of users with which the contract will execute) are entered into the contract.
- Each sender randomly generates an ephemeral elliptic curve key pair. The public key of this pair is sent to the intended transaction recipient. The two parties then generate a shared secret as in the stealth address protocol, and the sender submits the freshly formed public key to the ring mixing contract.
- Along with the freshly generated public key, users wishing to participate in the mix send the agreed denomination of the cryptocurrency, for example 1 Ether, to the contract. When a sufficient number of users have sent their public keys to the contract, with sufficient defined in respect to the original contract parameters, users can read the list of public keys which together form the ring.
- Each intended recipient can construct the secret key corresponding to a public key submitted to the contract. If the mix user is simply someone wanting to mix their coins, rather than transfer the coins into a recipient’s account, the user can still generate an ephemeral key pair and create a new stealth address for their coins to be transferred into.
- Intended recipients send the signature to the contract. The signature includes a tag, which is unique to each signer, message, and ring.
- The contract verifies that the tag is formed correctly, corresponding to one of the public keys in the ring. The signature and tag will only verify if:
- The message signed is the correct message,
- The ring in question is correct,
- The tag is correctly formed,
- The tag has not been seen before.
- Funds are released to each sender of a verified signature and tag.
There are grittier details about adding opcodes to the EVM, hashing to secp256k1, indistinguishability and random oracle assumptions, etc, but we’ll gloss over them here!
Combining cool thing #1 and cool thing #2
The combination of stealth addresses and ring signatures makes revealing blockchain anonymous almost impossible (in cryptography the property is generally referred to as infeasibility). Combining these two techniques, we arrive at a scheme that satisfies the following properties:
- Anonymity: The probability of an adversary identifying who created a transaction is at most negligibly higher than if the adversary were to guess entirely at random.
- Efficiency. The transactions take less than a second to generate, and when used with Ethereum’s ~15 second block time, your transaction could be mined before a ZCash zkSNARK has even finished generating 😉
Now breathe. And please tell me if you hated everything I said or have a million questions or want to let me know I’m wrong in a thousand ways!!!! (Or if more animal pictures are required).
Pingback: Blockchain Privacy – Part 2: Stealth Addresses | Financial Cryptography, Bitcoin, Crypto Currencies, Cryptanalysis