The return on investment = +233% in one year compared to +100% for bitcoin. More on this topic.
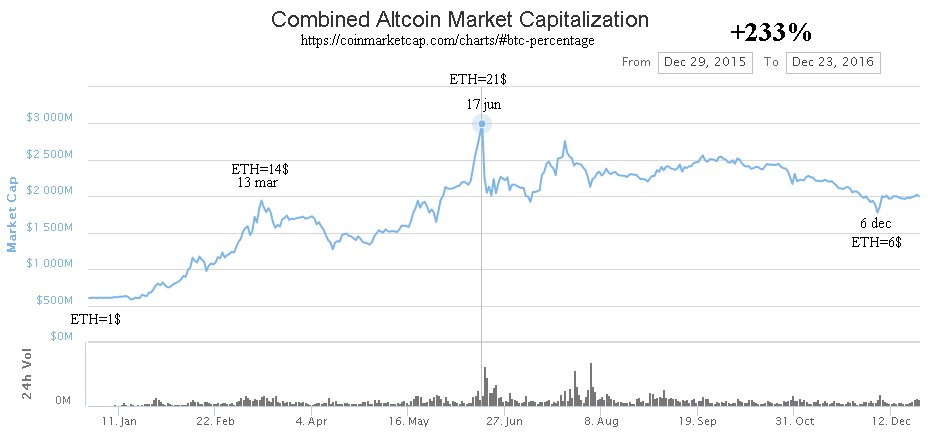 We see that the year 2016 was dominated by Ethereum. The year 2017 could be the year of Z.Cash.
We see that the year 2016 was dominated by Ethereum. The year 2017 could be the year of Z.Cash.
Blockchain Privacy – Part 3: Ring Signature Mixes
Now we’ve covered why privacy is essential for widespread cryptocurrency adoption, and how stealth addresses can help assist the pseudonymity (stealth addresses defined and explained in Part 2, pseudonymity discussed in Part 1), it’s time to explain how to combine cryptography and Ethereum’s smart contract functionality to add another layer of obfuscation to public blockchains!
COOL THING 2: RING SIGNATURES
Ring signatures generally satisfy several essential properties, namely anonymity, unforgeability, and collusion resistance. The definition of anonymity here is that an adversary has no more than a negligible advantage of correctly identifying the individual that produced the signature.
Ring signatures offer honestly participating users with ‘unconditional anonymity’, and are formed without a complex setup procedure or the requirement for a trusted third party, trusted setup, or any form of group leader. Users are simply required to be part of an existing public key infrastructure.
Ring signatures are constructed in a way that the ring can only be ‘completed’, and so will only verify correctly, if the signer has knowledge of some secret information, most commonly a private key corresponding to one of the public keys in the ‘ring’. This is done through a zero-knowledge proof of membership.
In the signature generation algorithm, a number is generated at random for each of the other public keys in the ring, and then the signer uses the knowledge of their own private key, or some other ‘trapdoor information’, to ‘close’ the ring.
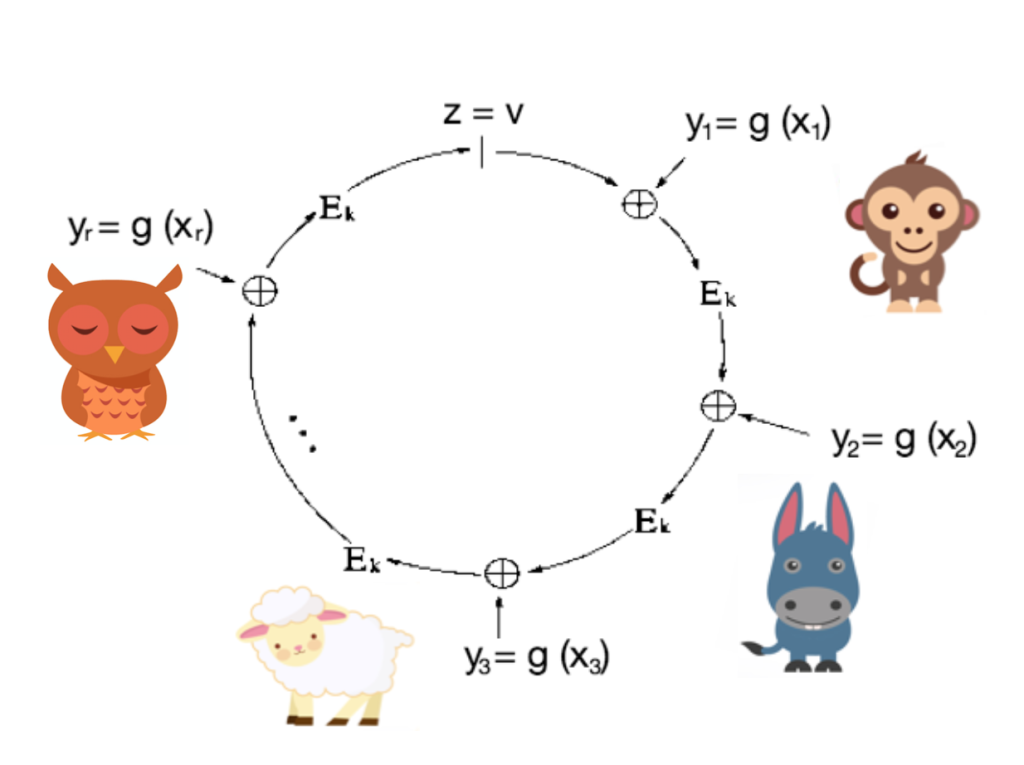
Ring signatures offer users anonymity by hiding transactions within a set of others’ transactions. If there are many users contributing very similar amounts to a ring, then the ring is said to have good liquidity, meaning the transactions can occur quickly, and also that transactions can be effectively mixed, with a high resistance to attempted mixing analysis attacks.
Linkable ring signature algorithms provide a scheme that allows users to sign on behalf of a group, again without revealing the individual signer’s identity, but with the additional property that any signatures produced by the same signer, whether signing the same message or different messages, have an identifier, called a tag, linking the signatures. With this tag, third parties can efficiently verify that the signatures were produced by the same signer, without learning who that signer is.
In our case, we use linkable ring signatures in a mixing contract.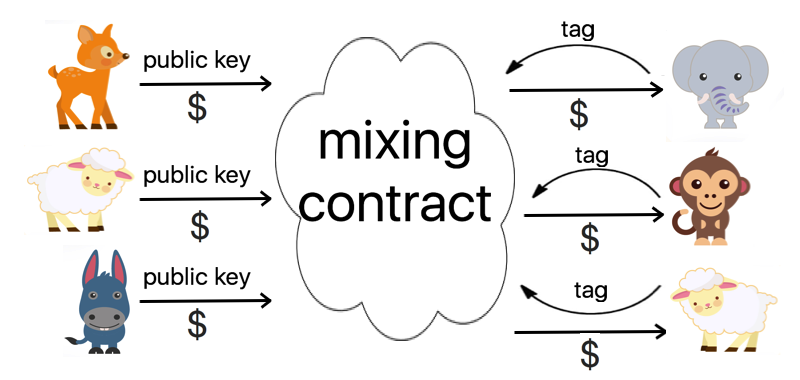
Ring Signature Mixing Contract
Our linkable ring signature scheme relies on the hardness of EC-DDH, and the general scheme is as follows:
- A contract is made to verify ring signatures, receive and distribute coins. Parameters for the specific mix (such as the transaction value of each amount to be deposited into the ring, or the minimum number of users with which the contract will execute) are entered into the contract.
- Each sender randomly generates an ephemeral elliptic curve key pair. The public key of this pair is sent to the intended transaction recipient. The two parties then generate a shared secret as in the stealth address protocol, and the sender submits the freshly formed public key to the ring mixing contract.
- Along with the freshly generated public key, users wishing to participate in the mix send the agreed denomination of the cryptocurrency, for example 1 Ether, to the contract. When a sufficient number of users have sent their public keys to the contract, with sufficient defined in respect to the original contract parameters, users can read the list of public keys which together form the ring.
- Each intended recipient can construct the secret key corresponding to a public key submitted to the contract. If the mix user is simply someone wanting to mix their coins, rather than transfer the coins into a recipient’s account, the user can still generate an ephemeral key pair and create a new stealth address for their coins to be transferred into.
- Intended recipients send the signature to the contract. The signature includes a tag, which is unique to each signer, message, and ring.
- The contract verifies that the tag is formed correctly, corresponding to one of the public keys in the ring. The signature and tag will only verify if:
- The message signed is the correct message,
- The ring in question is correct,
- The tag is correctly formed,
- The tag has not been seen before.
- Funds are released to each sender of a verified signature and tag.
There are grittier details about adding opcodes to the EVM, hashing to secp256k1, indistinguishability and random oracle assumptions, etc, but we’ll gloss over them here!
Combining cool thing #1 and cool thing #2
The combination of stealth addresses and ring signatures makes revealing blockchain anonymous almost impossible (in cryptography the property is generally referred to as infeasibility). Combining these two techniques, we arrive at a scheme that satisfies the following properties:
- Anonymity: The probability of an adversary identifying who created a transaction is at most negligibly higher than if the adversary were to guess entirely at random.
- Efficiency. The transactions take less than a second to generate, and when used with Ethereum’s ~15 second block time, your transaction could be mined before a ZCash zkSNARK has even finished generating 😉
Now breathe. And please tell me if you hated everything I said or have a million questions or want to let me know I’m wrong in a thousand ways!!!! (Or if more animal pictures are required).
Blockchain Privacy – Part 2: Stealth Addresses
Privacy
In Part 1 we covered why privacy is essential for widespread cryptocurrency adoption, and concluded that neither Bitcoin nor Ethereum, or even ZCash is suitable for the task we’re wanting to solve: anonymity with efficiency. (Also the bonus property of needing no trusted setup)!
COOL THING 1: STEALTH ADDRESSES
The benefits of using stealth addresses can be explained through this slightly contrived example:
Say Alice has a store, and she has her public key stuck to her till, so people can make payments to her in bitcoin/ethereum/ZCash. Alice is aware of the transaction analysis that people can perform on public blockchains, and her competitor Eve knows that about 98% of store payments are in Ether, so if she tracks Alice’s blockchain address, she will be able to monitor how Alice’s business is doing in near-real time. This makes Alice’s business vulnerable. For example, Eve could even learn to predict when Alice runs out of stock and then sell items to Alice at an unfair price. Instead of Alice changing her public key sticker every day, she can use stealth addresses!
Stealth addresses work as follows:
Say Alice has long-term, publicly known public key , and corresponding private key
, such that
, with
the generator of an elliptic curve (EC) group (if you don’t know what that means, we can just pretend they’re coordinates plotted on a graph with the property that
is an excessively obscure representation which does not reveal the secret
).
is an elliptic curve point (as is
— it’s defined along with the curve we’re working on) and
is a 256 bit integer.
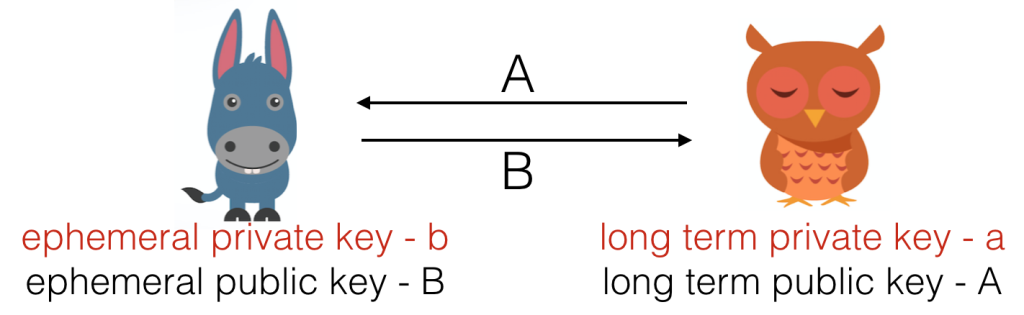
Bob wants to pay Alice. Normally he would just send Ether to Alice, but as we know, blockchain analysis would make this transaction entirely public. So instead, Bob’s wallet generates an ephemeral key pair, for use in just this one transaction, with an elliptic curve point, and
a 256 bit integer. Bob (or Bob’s wallet, acting on his behalf) sends
to Alice, and they can both calculate the shared secret
.
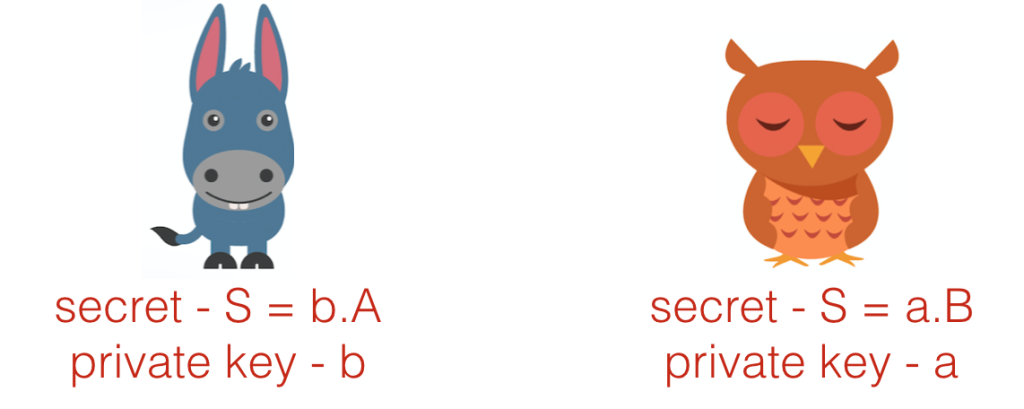
Bob can then send the Ether to an address formed ) (…with
being the function used to map from public keys to public addresses in Ethereum), and Alice can spend the money with private key
.
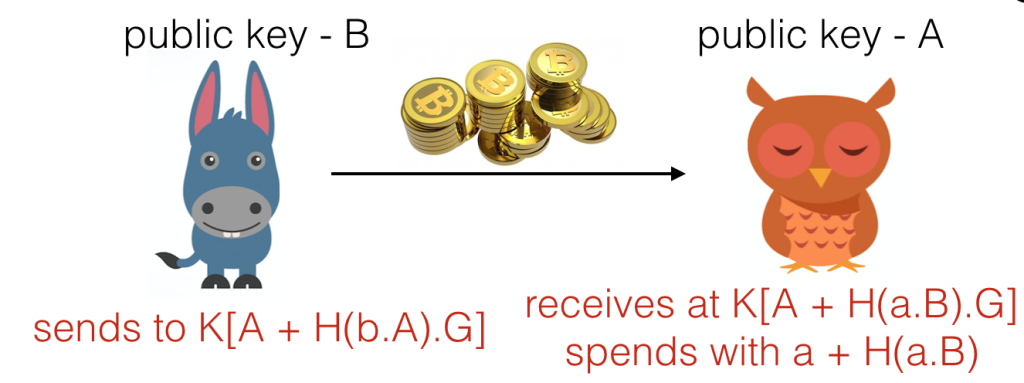
For any eavesdropper to compute the shared secret , they would have to crack the ECDH (elliptic curve Diffie-Hellman) problem. This is infeasible. So Alice’s privacy is protected so far!!
While we’re here, here are the definitions of ECDLP & EC-DDH. Both are useful in different parts of our huge scheme. The assumed hardness of the ECDLP is essential for privacy in the stealth address system, and the hardness of EC-DDH is the requirement for our ring signature scheme, described in Part 3. Assume E here is for Eve, our adversary (conventionally, the adversary is called A for adversary, but we have as Alice’s public key, so we can call the adversary E to avoid confusion between E, the malicious actor, and
, the elliptic curve point).
Definition 1 Elliptic Curve Discrete Logarithm Problem (ECDHP)
E has no advantage in solving following:
Given and
,
find .
Definition 2 Decisional Diffie-Hellman Assumption (EC-DDH)
E has no advantage in the following:
Given , with
, decide whether
.
Although the maths may look somewhat difficult to follow, Bob can send his one-time-use public key in the ‘data’ slot of the transaction, and so Alice can simply scan all transactions, find B, form the stealth private key, and spend the money as she wishes. The extra computations can all be automating inside and Alice and Bob’s wallets, and the communication is compressed down into 1 transaction needed, just like an entirely transparent result. This functionality is entirely possible with Ethereum & any wallet with stealth address capabilities.
However, if Eve is transferring money to Alice, and is really invested in finding out Alice’s income, she could produce a transaction (or many dust transactions) with stealth addresses for Alice, and then monitor the blockchain to see if Alice ever joins those accounts together or with others, in order to make an input to a higher value transaction in the future. This sounds unlikely to be relevant, but blockchain analysis (such as taint analysis) has been known to have crippling effects on the anonymity of public blockchain systems.
So we will work to prevent it. Using cool thing number 2.
D-Day For Z.Cash

Today the first ever truly anonymous crypto currency ZEC went live. The full P2P client can be downloaded from here [Linux only for now].
The total number of ZEC coins will be only 21 million, like in bitcoin. Zerocash also reproduces few other unreasonable properties known from bitcoin: bizarre monetary policy with inelastic monetary supply and block halving every 4 years, get-it-rich-quick or “gold rush” syndrome, etc. All the things which make a crypto currency with very high volatility, which I anticipate will be AT LEAST as bad as for bitcoin, and probably a lot worse. This of course, will be a tremendous barrier for wider adoption of Zerocash by people other than libertarians or tax dodgers.
Volatility Stage 1: Klondike Revisited
 Early miners are already selling their coins. To start with, Poloniex has started trading them at UNBELIEVABLY large prices and only tiny fractions like 0.001 ZEC were traded. In the first hour and half, prices were moving like crazy between 500 and 3000 BTC per ZEC. In the next hour it went below 20 BTC, in the next 24 h it went below 5 BTC, and after another 24 hours, it went down to 1 BTC.
Early miners are already selling their coins. To start with, Poloniex has started trading them at UNBELIEVABLY large prices and only tiny fractions like 0.001 ZEC were traded. In the first hour and half, prices were moving like crazy between 500 and 3000 BTC per ZEC. In the next hour it went below 20 BTC, in the next 24 h it went below 5 BTC, and after another 24 hours, it went down to 1 BTC.
It is worth noting that the Zerocoin price as anticipated by a prediction/futures market has peaked at around 1 BTC in the days/hours preceding the release.
Volatility Stage 2
It is unlikely that an equilibrium market price will be reached in the coming days. We expect further very high volatility for Zerocoin. The monetary policy of Zerocoin is genetically programmed to impose a certain pattern [known in advance] of progressively increasing monetary supply to the infant market. In particular, ZEC has artificially small block mining rewards for the first 34 days of mining. At the same time crypto currency investors have hundreds of millions of dollars in cash to play with, and many investors have been investing in altcoins rather than bitcoin. This is because traditionally altcoins are more volatile than bitcoin, so more profits can be made from trading. Moreover, maybe the only way for some investors to hope for really fabulous returns is to see some altcoin challenge the dominant position of bitcoin in the market.
Though only fools bought Zerocoins early on, many investors are now playing the game of guessing at which moment in ZEC history will be the best moment to buy, which question has no objective answer as it depends on actions of other investors.
Future Market Expectations
Zerocash certainly adds value to the cryptocurrency market. Now the question is how much is the added value? Here is a plausible evaluation and a plausible scenario for the future of ZEC:
- For some time it will be just a game where foolish investors are going to jump-start a (decreasingly) profitable mining market. In my opinion for now, Zerocoin is worth zero, in fact the system does not even work properly yet.
- The crypto currency market is today worth about 10 Billion USD. Now, not every user or miner of crypto currency cares about high levels of privacy. We conclude that the added value will be not more than a small fraction of 10 G$.
- I believe that Zerocash can hardly hope to achieve and sustain a 100M-ish market cap in the coming months, similar to what Monero has already achieved, which is maybe a fair measure of how much the market value an anonymous crypto currency in 2016.
- Achieving a similar result within a few months will be already a great success for the Zerocash team.
- The aforementioned futures market can apparently be seen as a bet on sth like 350M$ market cap at the end of 2016, cf. here. Probably by far too optimistic.
- Then only within a few years, the market cap of ZEC is likely to know some organic growth and larger adoption, and then it should be worth billions of dollars.
Will ZeroCash Be Banned?
An interesting question is whether some government [United States, EU, maybe Russia] is going to ban or forbid zerocash. Such a ban could be decided just because the production of money is according to some, a state monopoly in the United States. This is however largely disputed and for example bitcoin is tolerated today in most countries.

In contrast, a truly anonymous crypto currency could be just banned in many jurisdictions. While bitcoin is very rarely claimed to be a threat to national security (even less to the US currency), ZeroCoin is definitely a huge challenge to national security. It could lead to a re-definition of the term of so called “domestic terrorism”, which term was quite surprisingly used in the Liberty dollar case where it was rather totally inappropriate (cf. here). However anonymous crypto currency is such a tremendous threat to the established legal and financial order, taxation, and such a powerful enabler for organized crime, that we should expect legislators to introduce new specific forms of crime related to anonymous digital currency. Interestingly, Zerocash allows also for non-anonymous usage.
Illustrations are under 123rf licence.
Controversy Around Profitability of AltCoin Investment
There is a considerable controversy around whether investing in a balanced basket of cryptocoins is a good idea.
Two serious sources show that this sort of investment enjoys steady growth without a lot of downturns, cf. DLT10 Index and a recent detailed study which concentrates on a shorter period with excellent returns since Jan 2016 (cf. also this curve for the whole of 2016).
A rebuttal paper was published by Coindesk: over a period of a few years, bitcoin is claimed to outperform altcoins.
Oligarchy vs. Innovation
I would like to insist on the moral aspect of investment and what it means for the jobs in the technology sector.
By investing in medium-sized altcoins, we make blockchain better and bring a lot of innovation and truly advanced technology to the market:
- smart contracts with Ethereum,
- ring signatures and stealth address payments with Monero,
- zero-knowledge proofs with Zerocash,
- monetary policy innovation with Bitshares,
- etc..
By investing in bitcoin alone, we promote stagnation and poor technology which is barely trying to get better. A dystopian financial network which does not function well. Bitcoin is the “Microsoft of cryptocurrency”, cf. interview by Dr Courtois in Nature, it has a toxic culture, it is owned and controlled by China, it has a bad habit to censor the dissident voices, it uses super-dodgy cryptography, and it is simply sad that bitcoin will at times outperform its competitors.
Notes:
Many properties of bitcoin are self-defeating[Courtois] and lead to a programmed decline of bitcoin for example through skyrocketing fees [+557% in 2016!]. A very interesting curve to study is the so called bitcoin dominance curve. At moments bitcoin dominance reaches a peak [e.g. in Jan 2016 and again in Jan 2017]. Then it will reach a minimum, which happened in mid-March 2016 with the explosion of the Ethereum market. The long term trend is also, well less bitcoin dominance, more place for altcoins, which IMHO are THE investments which create some real value in this market. Let a thousand flower bloom.
How Many 1024-bit Primes Have Backdoors?
So how did the NSA backdoored the Internet or did they???
New ground-breaking paper shows that DSA and DH mod P keys with 1024 bits are vulnerable to practical backdoors which can be exploited to break our secure communications.
Few highlights:
- For such trapdoored primes the DL problem can be solved in 2 months by an academic cluster.
- The work is quite technical and improves on Crypto’92 paper by Gordon.
- New result is a lot stronger than recent work by Wong and Dorey-Chang-Fong-Essex where the number was not prime, which are also very common problems on the Internet.
- There is no known detection method for such trapdoor primes, or not yet.
- So if this sort of backdoor exists today, it is likely to remain hidden for yet some time.
-
- However researchers have also found a handful of primes used on the Internet and which are backdoored in a trivial and detectable way.
- There is a strong suspicion that many of currently used primes on the Internet are of dubious origin. We have lots of “opaque standardized” prime numbers used in many security standards.
- For example 37% of the Alexa top 1M web sites use primes which are hardcoded in Apache and nobody knows if they are not trapdoored.
- Similarly in May 2015, 56% of HTTPS handshakes have used a restricted set of primes which are controversial and many could be bugged.
- The only plausible defense at this moment is provably random nothing-up-my-sleeve primes such as defined in TLS 1.3. and some other security standards.
- It is also important to see that these problems concern primarily users and systems which do not apply latest NSA/NIST and other security recommendations (unhappily most people don’t).
Discussion
This is a SPECTACULAR reversal for the recommendation given by Bruce Schneier in Sep 2013 after being given the privilege of examining the bulk of unpublished Snowden files:
- “Prefer conventional discrete-log-based systems over elliptic-curve systems; the latter have constants that the NSA influences when they can”, see here.
The impact is also MUCH LARGER than with ECCs: a much larger part of the Internet communications is encrypted using “conventional discrete-log-based systems” than with ECCs (their share is about 10%).
UCL InfoSec Visit at Bletchley Park – 2 Oct 2016


Home Work
After a bombe demonstration by a WW2 veteran Ruth Bourne and BP bombe experts,
students have been asked to further study at home how Enigma was broken, see our hand-out.
More details can be found in our teaching materials “Enigma and Block Ciphers – 100 years of cryptanalysis with non-commutative combinations of permutations” which slides are studied in UCL COMPGA18/COMPM068 course Cryptanalysis.



A Series of Cash Bounties on Bitcoin Cracking
There is currently a series of little pots of bitcoins available for hackers to take. A whole series with an increasing difficulty level, see here.
Changing the Past of Ethereum – Not an Ordinary Divorce
Tomorrow 20 July Ethereum are going to invalidate more than 50M$ worth of Ethereum stolen by some rogue hacker group.

Congratulations to our community for this brave decision!
Support for this decision must be shown by all honest citizens of crypto space by upgrading ASAP geth.exe and mist wallets to the new version, for example now, and voting FOR THE FORK and against the illicit gains.
Remarks
This will NOT be the end of the story, as people who do NOT agree will be operating their own fork of Ethereum. There is a lot of sympathy out there for this sort of organized hacker groups which exhibit a high level of skills and ability. So we will have TWO Ethereum blockchains: the normal official Ethereum blockchain and a darker less well supported version of it. We expect that starting from tomorrow both chains will operate. Or the old chain will operate for some time until it possibly declines [or not].
Questions:
- Discarding the obsolete Ethereum clients not yet upgraded, will there be enough peers to support the second peer network which does not support the fork?
- Will some bitcoin exchange also list the “other” Ethereum coins???? Will the market share of Ethereum be divided in two separate market capitalizations? Will the supporters of dark forces actually succeed to steal some business from Ethereum???
A Messy Divorce
EDITED and ADDED 24-27 July 2016.
YES! We have the dark/old/orphaned/illegitimate Ethereum coins trading. Poloniex has started listing them under the name of ETC = Ethereum Classic. Also Bitfinex lists them.
- On 24 July we had 1 ETC = 0.065 ETH. At this moment the bounty was no longer worth 50M$ and it became 3M$ and it was quickly decreasing, it went down -85% in 24h.
- On 26 July however the illegitimate Ethereum went up by 400% in ETH value. By 3PM UK time it raised to 0.23 ETH. The ETC trading volume on Poloniex has exceeded the ETH volume [and any other coin daily volume].
- On 27 July the price of ETH has oscillated around 0.18 ETH which is remarkably close to the percentage of ETH holder who opposed the fork.
It is very difficult to explain what is going on here. Few points:
- Initially, most of ETC are not those which belong to some hackers. Most holders of ETH also automatically have ETC and they will also be selling them in panic, possibly.
- It is easy to see that most people who have these assets would NOT for some time realize that they have them, and they do not realize that they can sell them making some unexpected extra money and still keep their ETH. Most holders of ETH simply have not heard about a separate asset ETC that they now have and can sell it.
- We expect increased criminal activity overall in ETH blockchain in the coming days, why, because in order to sell these assets as their price goes down rapidly, people have to unlock their wallets, dig out their private keys from cold storage, or type in passwords etc. Now these are the same private keys as in the main ETH blockchain, already more valuable, so just having lots of people trying to sell whatever is left of their ETC will be a juicy time period for hackers to steal these private keys and withdraw money from both sides.
- Also replay attacks against ordinary ETH users are possible, cf. here.
- ETC is an illegitimate clone of Ethereum which has essentially stolen some 20% of their market share from Ethereum developers and all people who work hard on FinTech applications of Ethereum. It is a sophisticated form of theft or free-riding which now went far beyond just stealing 50M$ from the DAO owners.
- The question of who is buying these coins [90M$ volume in 24h] is a mystery.
- ETC has at moments become very interesting for miners, as initially most miners deserted it and some could earn more. ETC is also at risk of 51% attack by miners in ETH community. Now in a space of hours the hash rate of ETC has increased so much that the risk is no longer taken seriously [which is rather a bet that miners are probably too good, or too naive, or not well organized enough to do such an ugly thing].
- This shows that ETC exists because some wealthy miners and other important people support it. Many people were shocked to learn that Vitalik partly supports the fork, promises to tolerate it, and even gave some advice to the team which will support this fork from now on.
Remarks/Related: This older blog post by Dr. Courtois regarding a crypto currency divorce/splitting into two is cited, cf. pages 49 and 84, in a report by the British government Chief Scientific Adviser, Sir Mark Walport, “Distributed Ledger Technology: beyond block chain, here, 19 jan 2016.
Bitcoin Block Reward Halving
In a few minutes, cf. countdown, the amount of bitcoins attributed to each block mined will be divided by 2 in one single step. A rare event which happens once approximately every 4 years.

This is an artificial shock which is tolerated by the bitcoin community in the name of misplaced ideology that whatever was decided by Satoshi Nakamoto is brilliant and should not be changed.
However programming a sudden jump in a monetary policy of a crypto currency is a terrible engineering blunder and simply a very bad thing to have.
Does It Matter?
In the short term it will probably have positive effects:
- The supply of freshly mined bitcoins will halve. If the demand for these bitcoins remains constant, the price of bitcoin should increase (!!!).
- The unreasonable miner subsidy for each bitcoin transaction = the amount of money spent by miners to mine [frequently at a loss] in order to support bitcoin will decrease. Less “madness” means, well healthier bitcoin!
On Miner Subsidy
Bitctoin has this peculiar property that miners mine at a massive scale to support a relatively small payment network, compared to more traditional [centralized] payment systems.
Why did we call this madness???
They have never been in a human history a financial system in which each new transaction would require such incredibly large subsidy per transaction, imagine that I sent 10$ do someone using bitcoin. In order to make this transaction work miners have spent a few dollars mining. This is the cost for one single transaction to be included in the blockchain. This depending on its size in Kbytes, the current price of bitcoin, and block reward [to be divided by two now].
This is paid by newly created coins, or as some people have claimed by “debasement” of the currency. More coins means less value potentially for current coin holders. In fact NOT necessarily: the currency do actually appreciate because the bitcoin economy grows.
We could call this seigniorage cash flow or seigniorage income which pays for the network to function. The problem however is that it is quite expensive. It is a very unusual way to pay for a payment network to function here by mining, more or less for profit, or maybe rather at a loss. Seigniorage income is not a pure income without a cost, or income does not equal profits or net income after all expenses deduced. In fact the usual definition of seigniorage is the amount which is the difference between the money face value and the cost of its production. Here this difference is frequently negative [which is not totally unusual, for example many metallic coins are manufactured at a loss by central banks, they cost more to manufacture than the face value]. However someone must pay the bill, there are here questions of altruism, [positive] externalities and hidden subsidies in the crypto currency economy.
Long Term Effects?
Eventually the effect of this is probably a decline of bitcoin in the medium and long term. Why?
- A system with such incredibly large subsidies as explained above poses serious questions about their sustainability.
- Many other properties of bitcoin are SELF DEFEATING: they are toxic to bitcoin and its adoption.
- For example volatility implied by sudden shocks such as current block halving, while the halving could be much more gradual, see Section 13 of this paper.
- Lack of serious protections against 51% attacks and simply bad engineering is THE primary reason why bitcoin is slow. It is because of the risk [real or perceived] that people have to wait for many confirmations to accept payments in bitcoin. Bitcoin is not quite yet the Internet of Money, it is the “Horse Carriage of money” [said in the interview by Dr. Courtois for the Financial Times in 2014].
- Decline in miner income means that miners will be tempted to increase the fees to restore the profitability of mining operations. Increased fees means that people will prefer to use another crypto currency because of lower fees.
- The hash rate is expected to be divided by 2 overnight. Smaller hash rate means 51% attacks will be undeniably easier to execute and confidence in bitcoin could drop. It would be a good moment for bitcoin competitors to get some serious traction.
Hash Rate and 51% Attacks
An interesting question is: Will bitcoin hash rate be divided by two tomorrow?? This would be natural if miners were rational and miner profitability tended to some sort of equilibrium.
We are holding our breath. It can followed in real time here.
In the past the author of this blog has predicted that the hash rate of Dogecoin will be divided by 2 overnight, and this is exactly what happened, in fact it happened in the space of hours, actually it has happened MORE THAN ONCE, and exactly as predicted, in April 2014 and later, see Section 11.4 in this paper and here and here is a video.
BTW. The exact rule is NOT that it will be exactly divided by 2, but it has been a good approximation in the past.
To Decline or Not To Decline
Bitcoin and many other crypto currencies have been genetically programmed to self-destruct. This is undeniable, see this paper.
This “programmed” decline on bitcoin could be very slow and take 10-20 years.
But it could be also very fast, just because miners who are wealthy people with a lot of power influence, will simply decide to mine another crypto currency which is more reasonable [less “anomalous“] or more technologically advanced than bitcoin or simply faster, e.g. Ethereum.
On Strength of Bitcoin
However again, bitcoin is a DOMINANT crypto currency, and as such it will have a tendency to avoid the decline or not to decline. Bitcoin is the Microsoft of cryptocurrency. It enjoys a position of a natural monopoly with lots of positive externalities. A comfortable position which also makes bitcoin does not need to be particularly good at their business, just “good enough” [Antonopoulos LA bitocin meetup]. Some level of madness, or inability to reform/change/improve will not erode its dominant position. Other people need to work very hard to bring innovations and improvements to market, bitcoin doesn’t need to(!). It can cynically adopt them later when they mature.
For a longer discussion of the questions whether bitcoin is exempt from the “programmed decline” which is in the DNA of bitcoin, yet potentially the “dominant position effect” is yet stronger, we refer to Section 12 of our older paper.